Pico CTF 2025 [MEDIUM]
目次
PICO CTF 2025 ヒント通りに,Frida を使用して Sleep 関数のハンドラーを自動生成し, Windows10 VM に Python の venv を導入して,Frida を導入しています. 表示された base64 エンコード文字列を base64 デコードすると,Flag を入手できました. Easy だと分かりやすい問題が多かったですが,この問題には苦戦しました… このインスタンスは未攻略です.picoCTF 2025 Level:
Medium「Binary Instrumentation 1 : Reverse Engeneering」
exeファイルをダウンロードし,実行すると下記の文言が表示されそれ以外の処理はなされません.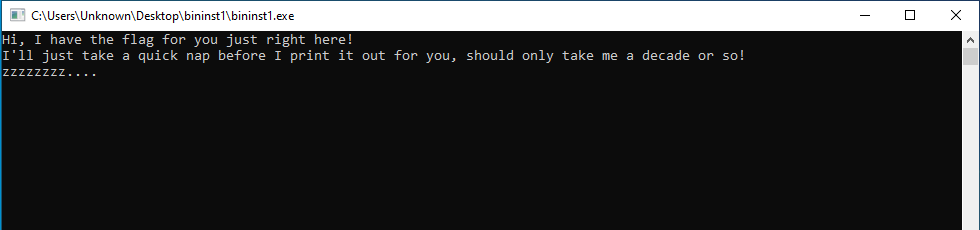
Sleep を解除するように改竄します.__handlers__\KERNELBASE.dll\Sleep.js/*
* Auto-generated by Frida. Please modify to match the signature of Sleep.
* This stub is currently auto-generated from manpages when available.
*
* For full API reference, see: https://frida.re/docs/javascript-api/
*/
;
C:\Users\Unknown\Desktop\venv> frida-trace -f "C:\Users\Unknown\Desktop\scan_exclusion_folder\bininst1.exe" -i "Sleep"
Instrumenting... e`...
Sleep: Loaded handler at "C:\Users\Unknown\Desktop\venv\__handlers__\KERNELBASE.
dll\Sleep.js"
Sleep: Loaded handler at "C:\Users\Unknown\Desktop\venv\__handlers__\KERNEL32.DL
L\Sleep.js"
Started tracing 2 functions. Web UI available at http://localhost:50083/
Hi, I have the flag for you just right here!
I'll just take a quick nap before I print it out for you, should only take me a
decade or so!
zzzzzzzz....
Ok, I'm Up! The flag is: cGljb0NURnt3NGtlX20zX3VwX3cxdGhfZnIxZGFfZjI3YWNjMzh9
/* TID 0x188c */
31 ms Sleep
31 ms | [*] Sleep called, original ms = -2
31 ms | [*] Sleep bypassed -> set ms = 0
:
:
:
31 ms Sleep
31 ms | [*] Sleep called, original ms = -2
31 ms | [*] Sleep bypassed -> set ms = 0
Process terminated
|
}
「Binary Instrumentation 2 : Reverse Engeneering」
File が含まれる関数(KERNEL32 のみ)を抽出します.
CreateFileA が使用されていることが分かりました. C:\Users\Unknown\Desktop\venv> frida-trace -f "C:\Users\Unknown\Desktop\scan_exclusion_folder\bininst2.exe" -i *File* -X "KERNEL32"
Warning: Skipping "FreeEncryptedFileMetadata": unable to intercept function at 00007FFFCEB29580; please file a bug
Warning: Skipping "_CrtSetReportFile": unable to intercept function at 00007FFFCF5A7BF0; please file a bug
Started tracing 546 functions. Web UI available at http://localhost:60691/
/* TID 0x1bec */
3528 ms NtDeviceIoControlFile
3528 ms RtlDosApplyFileIsolationRedirection_Ustr
3528 ms RtlDosApplyFileIsolationRedirection_Ustr
3528 ms RtlDosApplyFileIsolationRedirection_Ustr
3528 ms NtQueryAttributesFile
3528 ms NtQueryAttributesFile
3528 ms NtOpenFile
3528 ms RtlDosApplyFileIsolationRedirection_Ustr
3544 ms GetSystemTimeAsFileTime
3544 ms | GetSystemTimeAsFileTime
3544 ms GetModuleFileNameW
3544 ms | GetModuleFileNameW
3544 ms AreFileApisANSI
3544 ms | AreFileApisANSI
3544 ms CreateFileA
3544 ms | CreateFileA
Process terminated